Are You Ready for Ransomware?
Published: Nov 22, 2022
Last Updated: Jan 29, 2026
These days, everyone understands how important it is to have health insurance. Many may even think of it as a safety net that will prevent the worst—after all, that’s what insurance is for, right?
But as you might already know, having health insurance doesn’t necessarily mean you’ll escape sickness or escape paying anything to treat it. But that’s not the only thing you can do or have to help either. You can also prevent illness with the right healthy steps—a decent diet, regular exercise, and making sure you absorb some Vitamin D from the sun.
But you’ve also got to respond to any symptoms with a doctor’s visit so that you can ensure any sickness remains isolated with minimal effect and have routine check-ups to ensure that you remain accountable to your health goals.
That’s how you stay physically healthy, and interestingly enough, it’s also how you stay cyber-healthy (or secure) as well.
By this point, everyone knows about ransomware—it remains a huge problem for organizations, given that these attacks keep leveling up and growing more sophisticated (like a viral infection, if you will). Everyone-likely including you—also likely understands the basics of preventative measures.
But what about the other half of cybersecurity?
As a provider of cybersecurity assessments—including a new one that addresses said “other half”—in this article, we’re going to discuss what we mean. We’ll detail the importance of not just standard preventative measures, which we’ll discuss to an extent, but we’ll also cover incident response and recovery capabilities and why they’re more important than you think.
The Concern About Ransomware
Unfortunately, Trend Micro reports that the detection of attacks from ransomware-as-a-service surged in the first half of 2022, with new ransomware groups popping up all the time.
Highlights from cybereason’s report Ransomware: The True Cost to Business 2022 paint a bleak recent picture:
- 73% of respondents said they’d been targeted by at least one ransomware attack over the past 24 months (a 33% increase from 2021).
- Of those organizations that reported fallout from a ransomware attack, 67% said their financial losses totaled between $1 million and $10 million (USD).
That’s a lot of money that could be spent more beneficially, and it actually gets worse:
- Of the 28% who paid the ransom, 80% of them got hit with a second ransomware attack, and 68% got hit a second time within a month and for a higher ransom.
Despite cybersecurity evolving alongside the threat landscape, it’s more like a “when" not "if” situation when it comes to falling victim to ransomware or at least an attempted cyber intrusion.
The Two Angles of Ransomware Mitigation
What makes things worse is the current confusion in the cyber insurance world—prices are surging, coverage is shifting, and liability remains difficult to pin down. And you thought the health insurance market was tough to navigate.
But as we mentioned, being insured is only one helpful facet of protection against ransomware, and there are two others, which we’ll get into here.
1. Preventative Cyber Hygiene
These days, almost everyone has taken steps to prevent breaches and cyberattacks, so we won’t go too in-depth on those recommended tactics. You can check out our in-depth piece on how to build a comprehensive cybersecurity program and our CSET Ransomware Guide for more specific insight.
|
Protect Your Tech |
Educate Your Personnel |
Create Back-Ups |
|---|---|---|
|
|
|
2. Incident Response Procedures
Having good cyber hygiene can definitely lessen the likelihood of any attack, but having implemented effective response and recovery capabilities can also make a world of difference.
Think about it: should a ransomware attack hit you, once it kicks off, you no longer have time to plan—you don’t have time to consult with a lawyer regarding disclosure obligations, you don’t have time to find the money for the ransom, you don’t have time to sit down with your employees to discuss how to proceed.
(Moreover, when you’re hit unexpectedly with no plan in place, you can expect the price for help—given the probable immediate turnaround—to skyrocket.)
But by investing in ample incident response internally, you’ll panic less and can get right to work locating and isolating the attack before it can metastasize and spread further. Not only is isolating an event massive regarding minimizing potential consequences, but it’ll also streamline and help accelerate your recovery process.
Without proper incident response, an attack could spread to any corner of your organization, meaning you’ll have to:
- Check all your endpoints for vulnerabilities and likely re-image them;
- Sweep your all servers for residual problems and unauthorized access points; and
- Reissue multiple credentials across a variety of systems, among other clean-up necessities.
All that’s tedious, and for smaller and medium-sized businesses with fewer resources to dedicate to the effort, that might mean serious straining of your personnel and budget to get things done timely. (And your efforts will need to be timely because as with the statistics we reported earlier, a vast majority of businesses were hit a second time—most within a month.)
Can Our Ransomware Preparedness Assessment Help You?
But how to know if your incident response and recovery capabilities are adequate and designed to address recovery from a ransomware event? How to know your procedures will work without an actual attack happening to test them? That’s where our Ransomware Preparedness Assessment can come in.
We offer three different tiers of this assessment, and they vary based on your necessary effort and what kind of report we provide: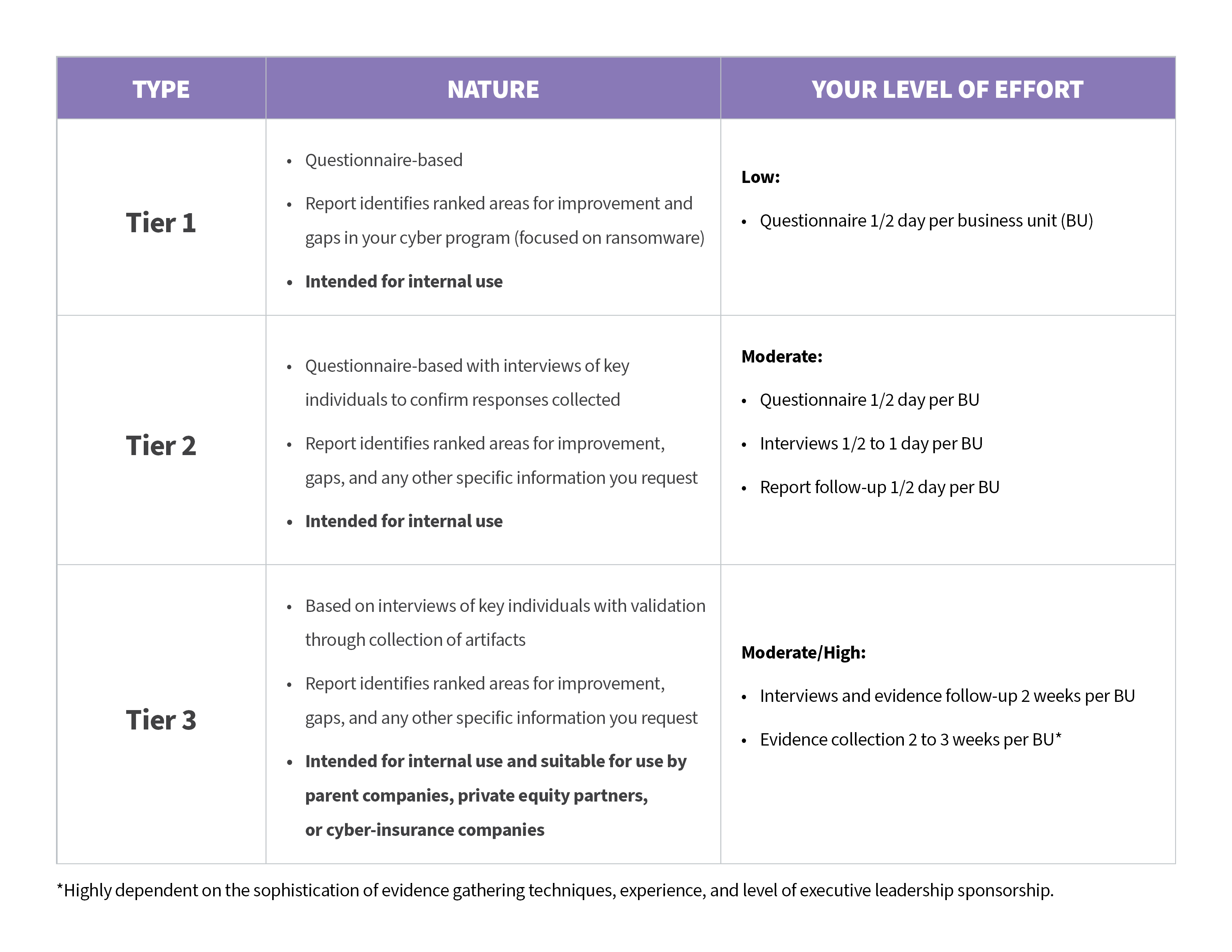
But no matter what level you choose, this assessment evaluates the whole of your ransomware prevention efforts—that’s general cyber hygiene (prevention) but with a real focus on your response and recovery capabilities so that you can be sure your plans for response and recovery are as well-rounded as they can be.
Our team would “assume a breach had occurred” and then essentially test your security incident management lifecycle. Through a questionnaire, interviews, and—depending on your chosen Tier as mentioned above—evidence collection over a maximum of 3 weeks, we can help you determine whether your organization truly is prepared for a potential ransomware event.
If your incident response practices parallel going to the doctor, think of our Ransomware Preparedness Assessment as a physical check-up designed to help you ensure accountability in your incident response and recovery capabilities.
And, not only can this extra step help you plug any remaining vulnerabilities and rest a little easier thanks to the independent verification, but this specialized assessment can also position you to move forward with more complex or holistic cybersecurity compliance initiatives like ISO 27001 or NIST CSF.
If you’re interested in learning more so you can truly discern if this independent evaluation of your ransomware preparedness is right for your organization, please contact us.
Moving Forward with Your Ransomware Defense
The technological landscape being what it is now, it seems likely that, on a long enough continuum, every company will experience a ransomware attack. Now you understand why, in your preparation against it, you’ve got to ensure you address both preventative measures and your incident response and recovery capabilities.
Our Ransomware Preparedness Assessment can go a long way towards helping you sleep better at night regarding where you stand while cybercriminals lurk about, but there are also other steps you can take to improve your cybersecurity, as well as other threats you should be aware of—we recommend these articles to further highlight the importance of building a security program that works for your organization and certain threats we think you should be aware of:
About Bryan Harper
Bryan Harper is a Director with Schellman. Prior to joining Schellman in 2017, Bryan worked as a Senior IT Auditor, specializing in SOC examinations. Bryan also worked as a staff accountant in a public accounting firm performing financial audits, consulting, and out-sourced internal audit engagements for clients in the banking, insurance, and healthcare industries. Bryan is now focused primarily on SOC examinations for organizations across various industries. At Schellman, Bryan is involved with technical training development specific to auditing cloud services and supports Schellman's cybersecurity task force, which is responsible for monitoring developments in and responding to cybersecurity regulations and related cybersecurity compliance frameworks.




