Including Colocation Service Providers When Scoping ISO 27001?
Published: Apr 10, 2023
Last Updated: Nov 9, 2023
Introduction
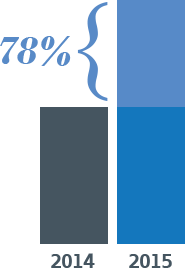 ISO/IEC 27001:2015 (ISO 27001) certification is becoming more of a conversation in most major businesses in the United States. To provide some depth, there was a 20% increase in ISO 27001 certificates maintained globally (comparing the numbers from 2014 to 2015 as noted in the recent ISO survey). As for North America, there was a 78% growth rate in ISO 27001 certificates maintained, compared to those in North America in 2014. So it is clear evidence that the compliance effort known as ISO 27001 is making its imprint on organizations in the United States. However, it’s just the beginning. Globally, there are 27,563 ISO 27001 certificates maintained, of which only 1247 are maintained in the United States; that is 4.5% of all ISO 27001 certificates.
ISO/IEC 27001:2015 (ISO 27001) certification is becoming more of a conversation in most major businesses in the United States. To provide some depth, there was a 20% increase in ISO 27001 certificates maintained globally (comparing the numbers from 2014 to 2015 as noted in the recent ISO survey). As for North America, there was a 78% growth rate in ISO 27001 certificates maintained, compared to those in North America in 2014. So it is clear evidence that the compliance effort known as ISO 27001 is making its imprint on organizations in the United States. However, it’s just the beginning. Globally, there are 27,563 ISO 27001 certificates maintained, of which only 1247 are maintained in the United States; that is 4.5% of all ISO 27001 certificates.
As the standard makes its way into board room and compliance department discussions, one of the first questions is understanding the scope of the effort. What will be discussed in this short narrative is something that we, as an ANAB and UKAS accredited ISO 27001 certification body, deal with often when current clients or prospects ask about scoping their ISO 27001 information security management system (ISMS), and specifically related to how to handle third party data centers or colocation service providers.
Scenario
Consider an organization is a software as a services (SaaS) provider with customers throughout the world. All operations are centrally managed out of one location in the United States but to meet the needs of global customers, the organization has placed their infrastructure at colocation facilities located in India, Ireland, and Germany. They have a contractual requirement to obtain ISO 27001 certification for their SaaS services and are now starting from the ground up. First things first, they need to determine what their scope should be.
Considerations
It is quite clear that given the scenario above, the scope will include their SaaS offering. As with ISO 27001, the ISMS will encompass the full SaaS offering (to ensure that the right people, processes, procedures, policies, and controls are in place to meet their confidentiality, integrity, and availability requirements as well as their regulatory and contractual requirements). When determining the reach of the control set, organizations typically consider those that are straight forward: the technology stack, the operations and people supporting it, its availability and integrity, as well as the supply chain fostering it. This example organization is no different but struggles with how it should handle its colocation service providers. Ultimately, there are two options – Inclusion and Carve-out.
Inclusion
The organization can include the sites in scope of its ISMS. The key benefit is that the locations themselves would be included on the final certificate. But, with an ISMS, an organization cannot include the controls of another organization within its scope as there is no responsibility for the design, maintenance, and improvement of those controls in relation to the risk associated with the services provided.
So, to include a colocation service provider, it would be no different than including an office space that is rented in a multi-tenant building. The organization is responsible for and maintains the controls once the individual enters its boundaries but all other controls would be the responsibility of the landlord. The controls within the rented space of the colocation service provider would be considered relevant to the scope of the ISMS. These controls would be limited, which is understandable given their already very low risk; however, they would still require to be assessed. That would mean that an onsite audit would be required to be performed to ensure that the location, should it be included within the scope and ultimately on the final certificate, has the proper controls in place and has been physically validated by the certification body.
As a result, the inclusion of these locations would allow for them to be on the certificate but would require the time and cost necessary to audit them (albeit the assessment would be limited and focused only on those controls the organization is responsible for within the rented space of the colocation service provider).
Carve-out
The organization can choose to carve out the colocation service provider locations. As compared to the inclusion method, this is by far cheaper in that onsite assessments are not required. More reliance would be applied to the controls supporting the Supplier Relations control domain in Annex A of ISO 27001; however, these controls would be critical for both the inclusive and carve-out method. The downside of this option – the locations could not be included on the final ISO 27001 certificate (as they were not included within the scope of the ISMS), and it may require additional conversations with customers highlighting that though those locations were not physically assessed as part of the audit, the logical controls of the infrastructure sited within those locations were within the scope of the assessment and were tested.
Conclusion
Ultimately, it is a clear business decision. Nothing in the ISO 27001 standard requires certain locations to be included within the scope of the ISMS, and the organization is free to scope their ISMS as it suits. Additionally, unlike other compliance efforts (such as AICPA SOC examinations), there is not a required assertion from the third party regarding their controls, as the ISMS, by design, does not include any controls outside of the responsibility of the organization being assessed. However, the organization should keep in mind the final certificate and if it will be fully accepted by the audience that is receiving it. Does the cost of requiring the onsite audit warrant these locations to be included or is the justification just not there.
If this scenario is applicable to your situation or scoping, Schellman can have further discussions to talk through the benefits and drawbacks of each option so that there is scoping confidence heading into the certification audit.
About Ryan Mackie
Ryan Mackie is a Managing Principal at Schellman, and has been with the firm since 2005. Ryan supports the regional Florida market and manages SOC, PCI-DSS, ISO, HIPAA, and Cloud Security Alliance (CSA) STAR Certification and Attestation service delivery. He also oversees the firm-wide methodology and execution for the ISO certification services, including ISO 27001, ISO 9001, ISO 20000-1, and ISO 22301 as well as CSA STAR certification services. He has over 25 years of experience. Ryan also is an active member of the CSA and co-chairs the Open Control Framework committee which is responsible for the CSA STAR Program methodology and execution.




